In the age of digital transformation, data is one of the most precious assets that a company can own. It generates insights, powers operations, and connects businesses to their customers. However, as firms become increasingly data-driven, the value of data security grows tremendously. In 2025, data security is about more than just preventing breaches; it’s also about maintaining trust, ensuring compliance, and creating a sustainable digital environment.
Creating and implementing strong security strategies is vital for safeguarding critical data while promoting innovation and business growth. This essay delves into the fundamentals of modern data security, such as encryption, secure APIs, regulatory compliance, and ethical data practices—all of which are critical for creating a resilient and trustworthy digital infrastructure.
1. Why Data Security Matters More Than Ever
Data breaches are no longer isolated instances but rather global hazards, as cyber threats become more frequent and complicated. Unsecured data can lead to the following:
- Financial Losses
- reputational damage
- Legal penalties
- Loss of customer trust
As a result, investing in data security is not an option; it is a must.
2. Encryption, the First Line of Defense
Encryption is a critical component of data protection. It ensures that sensitive data, whether at rest or in transit, remains unreadable by unauthorized users.
Key encryption types:
- Symmetric Encryption (AES) is fast and appropriate for internal data encryption.
- Asymmetric Encryption (RSA) is ideal for secure communication and authentication.
- End-to-End Encryption (E2EE) is utilized in messaging applications and cloud-based solutions.
Encryption not only secures data but also assists businesses in meeting compliance regulations such as GDPR, HIPAA, and ISO/IEC 27001.
3. Securing APIs for Digital Gateways
APIs (application programming interfaces) have become the foundation of digital ecosystems, allowing systems to communicate and share data. However, they can pose potential weaknesses if not properly guarded.
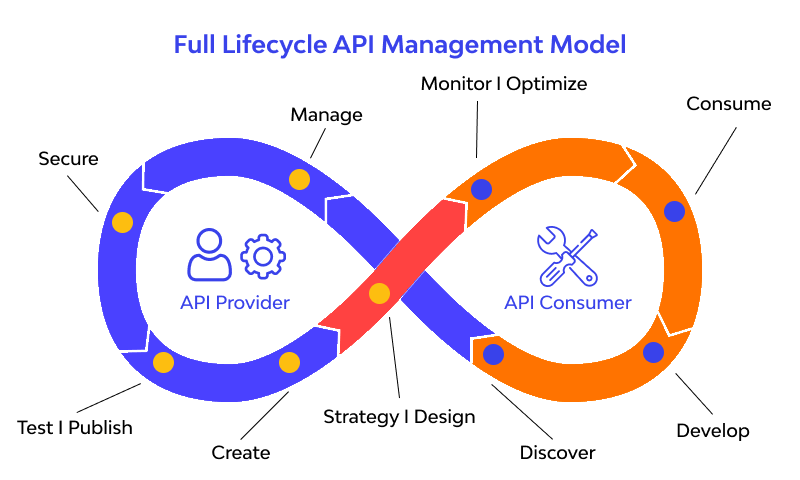
Best Practices for Secure API Management:
- OAuth 2.0 and JWT for safe authentication.
- Rate-limiting to prevent abuse
- Input validation to prevent injection attacks
- Token expiration policies to reduce session hijacking.
4. Compliance: Meeting Legal and Industry Standards.
Data privacy standards are growing increasingly stringent over the world. Businesses must now follow strict compliance requirements when collecting, storing, or processing personal and sensitive data.
Key regulations include:
- GDPR (EU) protects user data and privacy rights.
- CCPA (California)—Gives consumers more control over their personal data.
- HIPAA (USA) regulates healthcare data security.
- The DPDP Act (India) is a new personal data protection framework.
Failure to comply might result in significant fines and judicial action. That’s why we assist organizations in auditing their systems and building compliance-ready infrastructures.
5. Ethical Data Handling: Not Just Compliance
While legal compliance is crucial, ethical data handling extends beyond simply following the laws. It’s about protecting user privacy, being open about data usage, and prioritizing customers.

Principles of Ethical Data Use:
- Data reduction – Collect only what is necessary.
- Transparency: Clearly communicate how data is used.
- User consent: Allow users to opt in or out of data collecting.
- Accountability: Take responsibility for data practices.
Companies that stress ethical data handling strengthen consumer relationships and differentiate themselves as trustworthy brands.
6. Emerging Threats and Proactive Security.
Cyber threats will change dramatically by 2025. To keep ahead of threats such as ransomware and phishing, insider assaults, and zero-day exploits, firms must use proactive security tactics.
Modern security tools include the following:
- AI-based threat detection
- Multiple-factor authentication (MFA)
- Zero Trust Architecture includes cloud-native firewalls and monitoring systems.
We collaborate with businesses to implement current security procedures and protect all digital touch points.
7. Secure Your Digital Future
End-to-end data security is critical in today’s linked society. Effective protection demands a complete, proactive approach, not just isolated tools. Custom encryption implementations, secure API creation, regulatory compliance advising, and comprehensive cybersecurity risk assessments, including penetration testing, are among the key services offered. True security should be friction less, scalable, and forward-thinking—not a patchwork of tweaks, but a purposefully built system that grows with your company.
Conclusion:
Secure data, secure business.
In the digital age, data security is the cornerstone of trust, performance, and durability. As cyber dangers intensify and privacy expectations rise, firms that take a proactive, ethical, and thorough approach to data protection will be ahead of the curve. Do not wait until there is a breach to take action. Secure your systems today with solutions that are built for tomorrow.

